Automate IT Compliance Across All Frameworks with Intelligent MDM
Transform your compliance management with enterprise-grade compliance automation that monitors, enforces, and remediates policy violations across SOC2, HIPAA, GDPR, and CIS frameworks - all from a single platform designed for resource-constrained IT teams.
Ready to eliminate manual compliance overhead?
Automated Policy Enforcement
Deploy framework-specific policies across all managed devices with zero-configuration templates and intelligent rule application.
Real-time Compliance Scoring
Monitor your security posture with dynamic compliance scores that track framework adherence and highlight critical violations instantly.
Framework Templates
Access pre-configured compliance templates for SOC2, HIPAA, GDPR, CIS Level 1/2, ISO/IEC 27001, and industry-specific requirements.
Instant Remediation
Trigger automatic policy corrections and device remediation workflows when violations are detected, minimizing exposure windows.
How fast can you detect policy violations across your fleet?
Manual compliance monitoring leaves critical gaps in security posture assessment. Traditional approaches require dedicated compliance staff to manually audit device configurations, review policy adherence, and generate evidence - resources most SMBs simply don't have.
Intelligent Framework Management
Experience streamlined MDM setup with automated compliance deployment across all major frameworks and device platforms.


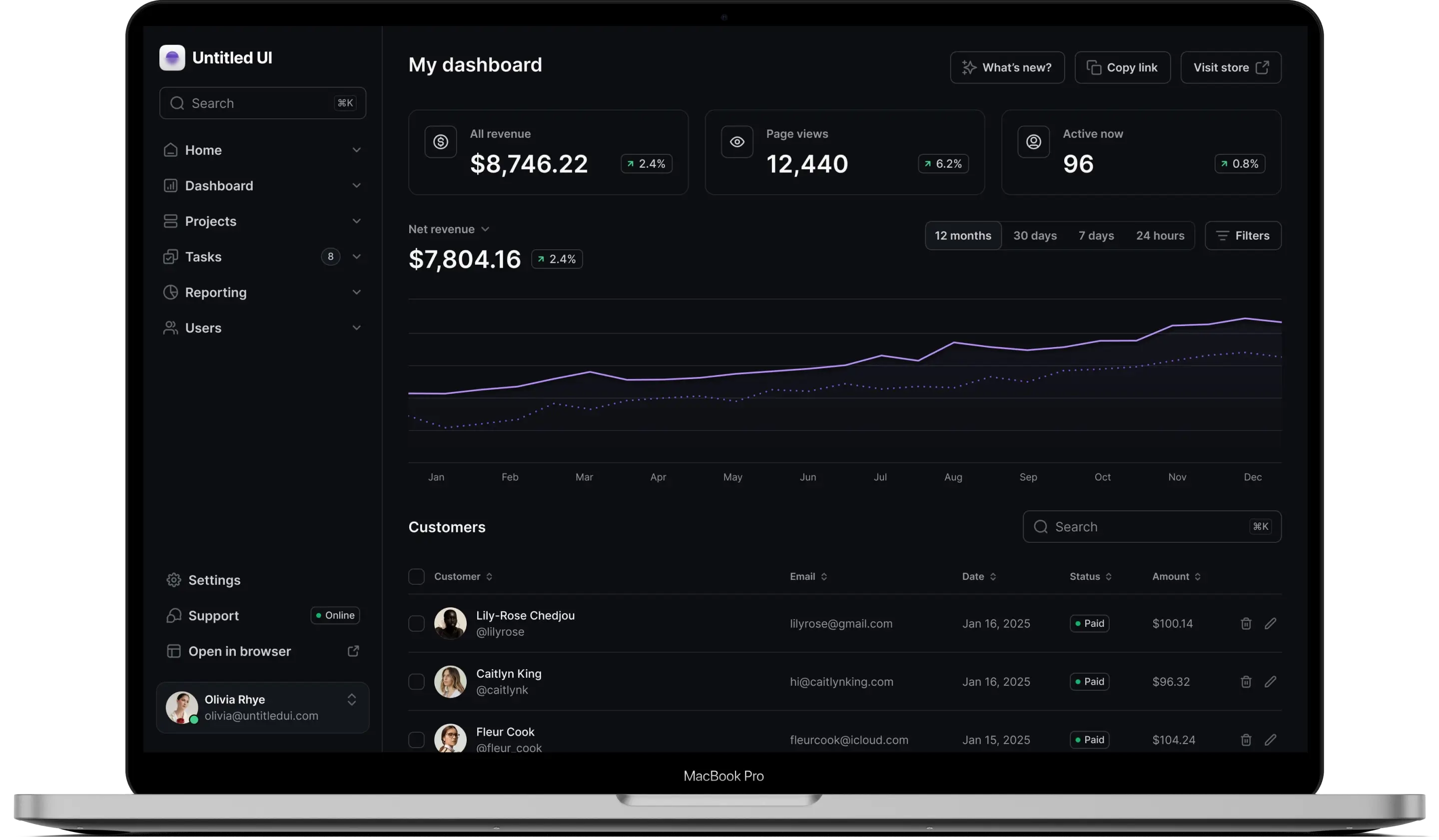
Multi-Framework Compliance Engine
Enterprise-grade security compliance automation designed for growing businesses that need comprehensive framework support without dedicated compliance specialists.
Implement comprehensive SOC2 Type II controls with automated evidence collection, continuous monitoring of security criteria, and streamlined audit preparation across all five trust service principles.
Learn moreDeploy healthcare-specific compliance controls with automated PHI protection policies, access control enforcement, and breach detection workflows designed for medical practice environments.
Learn moreEnforce European privacy regulations with automated data protection policies, consent management workflows, and right-to-erasure compliance across all managed endpoints and applications.
Learn moreApply Center for Internet Security benchmarks with automated configuration hardening, vulnerability assessment integration, and continuous security posture monitoring for Level 1 and Level 2 controls.
Learn moreImplement information security management system requirements with automated policy deployment, risk assessment workflows, and continuous compliance monitoring across organizational assets.
Learn moreCreate organization-specific compliance frameworks by assigning custom security controls, defining policy inheritance rules, and building automated remediation workflows tailored to industry requirements.
Learn moreContinuous Compliance Monitoring
Real-time oversight with intelligent reporting and automated remediation capabilities that keep your organization audit-ready without constant administrative overhead.
Deploy framework-specific policies across all managed devices with zero-configuration templates and intelligent rule application.
Monitor your security posture with dynamic compliance scores that track framework adherence and highlight critical violations instantly.
Access pre-configured compliance templates for SOC2, HIPAA, GDPR, CIS Level 1/2, ISO/IEC 27001, and industry-specific requirements.
Trigger automatic policy corrections and device remediation workflows when violations are detected, minimizing exposure windows.

Industry-Specific Implementation
Healthcare HIPAA Compliance
Automated PHI protection with medical device integration and clinical workflow optimization for healthcare environments requiring strict privacy safeguards.

Financial SOC2 Automation
Real-time transaction monitoring with data protection policies and regulatory reporting designed for financial institutions managing sensitive customer data.

Manufacturing CIS Controls
Operational technology integration with industrial device management and supply chain security controls for manufacturing environments.

Education FERPA Standards
Student data protection policies with classroom device management and educational technology integration for academic institutions.

Advanced Policy Architecture
Sophisticated compliance automation engine with intelligent policy orchestration and ML-enhanced violation detection for comprehensive security posture management.



Identity Provider Sync
Integrate seamlessly with Entra ID, Google Workspace, and Okta for automated user provisioning and policy assignment across identity management systems.
SIEM Platform Integration
Export compliance events and violation alerts to security information platforms through standardized APIs and webhook configurations for centralized monitoring.
Audit Evidence Automation
Collect compliance evidence automatically through integrated monitoring systems that capture policy events, configuration changes, and remediation actions for audit preparation.
Complete Framework Coverage
- Learn more
Regulatory Standards
SOC2 Type I and Type II with full Trust Service Criteria coverage, HIPAA Privacy and Security Rule implementation, GDPR Article 32 technical measures, and PCI DSS requirements for payment processing environments.
- Learn more
Security Frameworks
CIS Controls Level 1 and Level 2 with automated benchmarking, ISO/IEC 27001:2022 information security controls, NIST Cybersecurity Framework implementation, and custom organizational framework development.
- Learn more
Automated Evidence Collection
Generate audit-ready documentation with continuous evidence gathering, policy application logging, and compliance status reporting that satisfies regulatory examination requirements without manual intervention.

Ready to transform your compliance automation strategy?Start your free demo and discover how automated compliance monitoring eliminates manual overhead while maintaining enterprise-grade security standards.
Ready to transform your compliance automation strategy?Start your free demo and discover how automated compliance monitoring eliminates manual overhead while maintaining enterprise-grade security standards.
