Home Page
Automate Compliance Across
All Devices – Effortlessly
Trio ensures enterprise-grade security compliance across Windows, macOS, and more, powered by real-time automation.
 Cross-platform compliance: Windows, macOS, more
Cross-platform compliance: Windows, macOS, more Audit-ready reporting & custom compliance policies
Audit-ready reporting & custom compliance policies Automated remediation, real-time monitoring
Automated remediation, real-time monitoring

Key Solutions
Unified Device Management
Manage Android, iOS, Windows, and macOS from one intuitive dashboard. Onboard devices in minutes, enforce policies, and resolve issues remotely, all in one streamlined platform.
Security Built-In
Block threats proactively and stay compliant with SOC 2, HIPAA, GDPR, and ISO 27001 in real time. Instantly remediate risks with auto-lock, silent patching, and AI-driven endpoint security.
Endpoint Protection
Protect every device, office, remote, or on-the-go with silent patching and data loss prevention. Real-time alerts and automated lockdowns ensure fast, disruption-free security.
Industry Use Cases
Explore
our features
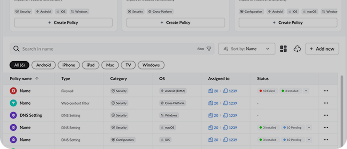
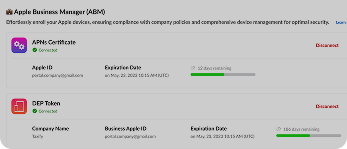
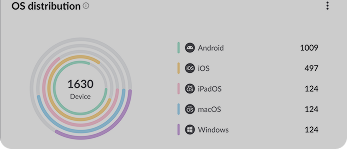
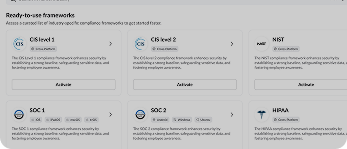
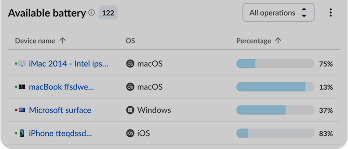
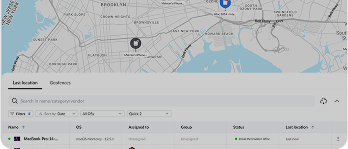
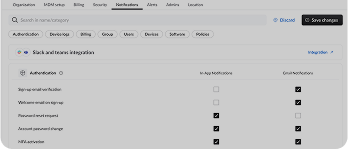
Ready to Automate
Your Mobility Stack?
Eliminate tool sprawl. Automate IT, secure every endpoint, and onboard in minutes, with one AI-first platform.

Windows Digital Signage Guide: Setup & Configuration Tips
Windows Digital Signage transforms standard Windows devices into professional display systems through kiosk mode configuration and specialized software. Any Windows...

UEM Migration: 5-Phase Implementation Plan for IT Admins
UEM migration transfers endpoint management from legacy MDM/EMM systems to modern unified platforms that manage all devices from a single...

The Ultimate Guide to BYOD Policies for SMBs
The debate surrounding Bring Your Own Device (BYOD) policies remains a pivotal consideration for SMBs across various sectors. According to...
Get a Custom Demo
Cut device setup time by 50% and eliminate security gaps — see how in 15 minutes.
- Tailored solutions for your industry
- Fast, zero-touch onboarding for all devices
- Instant compliance: track, lock, or wipe in one click
- Expert help—BYOD, scaling, migration, and more
By clicking submit below, you agree to Trio Privacy Policy and to receive marketing emails and phone calls from Trio. You may unsubscribe at any time.
- 14-Day Free Trial
- White-Glove Onboarding
- Free Migration Plan
- No credit card required