“While 84% of organizations globally experience BYOD practices, only 52% officially permit it.”
— Financial Times, 2023
As hybrid work environments become the norm, Bring Your Own Device (BYOD) adoption has skyrocketed. The global BYOD and enterprise mobility market is expected to reach $296.4 billion by 2030 (Research and Markets, 2023). While BYOD offers flexibility, cost savings, and convenience, it introduces serious risks, especially for small and medium-sized businesses (SMBs) with limited IT resources.
This is where Mobile Device Management (MDM) becomes essential. A modern MDM solution like Trio enables lean IT teams to manage personal and corporate devices through one unified dashboard to balance security with usability.
In this post, we’ll break down the top BYOD challenges facing IT admins today and offer real-world tips and solutions you can act on, without overcomplicating your tech stack.
TL;DR:
- Learn why unmanaged BYOD environments pose major compliance and security risks
- See how Trio MDM enforces policies across personal devices
- Discover BYOD best practices to protect data without slowing down teams
What Is BYOD?
“Over 80% of organizations now allow or use BYOD in some form.”
— Cybersecurity Insiders, 2023
Bring Your Own Device (BYOD) refers to a policy where employees (or students) use their personal devices, like smartphones, laptops, or tablets, to access company systems, apps, and data. Rather than issuing company-owned hardware to every user, organizations allow people to work on the devices they already own and prefer.
For small and mid-sized businesses, BYOD can cut hardware costs and increase flexibility, but it also creates new IT risks if left unmanaged.

The Upside of BYOD
Adopting a BYOD policy can offer major advantages, especially for resource-constrained IT teams. When properly managed with an MDM platform like Trio, BYOD boosts flexibility without compromising security or control.
Here are some of the key benefits:
| Benefit | What It Solves | Why It Matters for SMBs |
|---|---|---|
| Cost Savings | Reduces need to purchase and maintain company-owned hardware | Cuts CapEx; more budget for core priorities |
| Productivity Boost | Users are faster on familiar devices | Less training, smoother onboarding |
| Flexibility & Morale | Users can pick preferred OS or form factor | Increases satisfaction and retention |
| Latest Tech Access | Personal devices are often newer than company-issued ones | Keeps users on up-to-date platforms |
| Work-Life Balance | One device for both personal and professional use | Enables remote/hybrid work with fewer constraints |
| Innovation Potential | Exposure to a diverse set of apps and workflows | Encourages creative problem solving and adoption of new tools |
With Trio, you can embrace these benefits without the risk, applying encryption, compliance rules, and remote wipe across every enrolled personal device.

BYOD Concerns and Challenges
While the benefits of BYOD are clear, the risks can be just as significant, especially for small teams with limited resources. Even with best practices in place, IT admins must tackle multiple operational and security issues to keep data safe and devices compliant.
Here are the most pressing BYOD challenges and how MDM solutions like Trio help mitigate them:
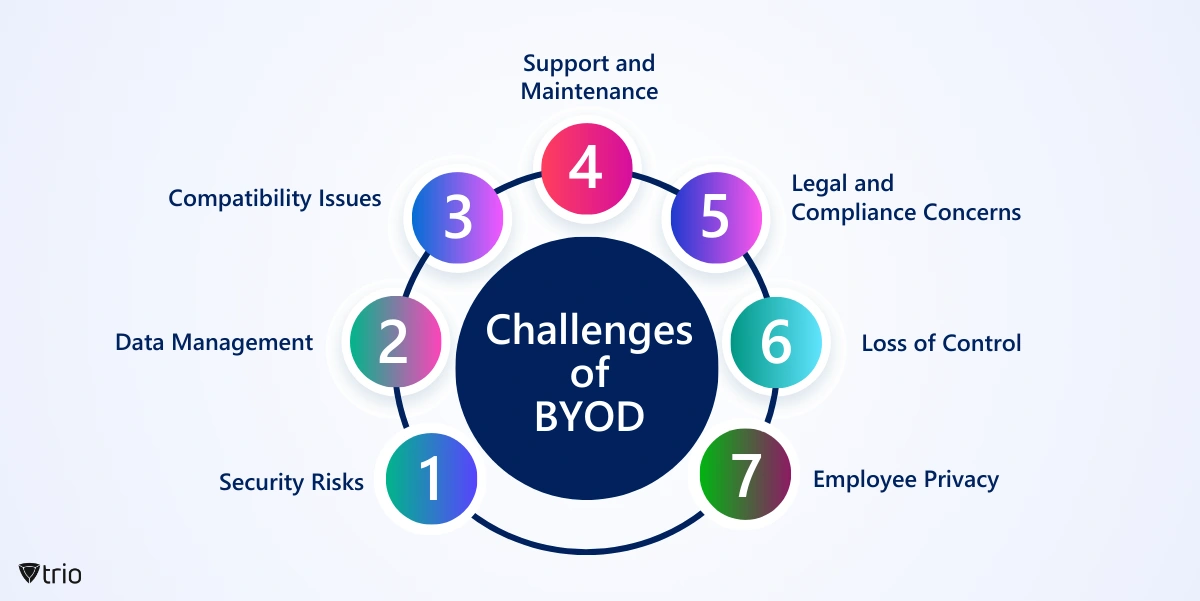
1. Security Gaps on Personal Devices
Why it matters: Personal devices often lack enterprise-grade protections, making them a soft target for malware, phishing, or unauthorized access.
Solution: Trio enforces full-disk encryption, auto-locks, and remote wipe, even on BYOD devices, to prevent data leaks before they happen.
2. Data Management Complexity
Why it matters: Without proper controls, sensitive business data may be stored, shared, or accessed insecurely.
Solution: Trio separates personal and corporate data via containers, allowing remote policy enforcement without affecting the user’s private content.
3. Compatibility & Interoperability
Why it matters: Devices running different OS versions or outdated apps can cause sync errors, crashes, or productivity bottlenecks.
Solution: Trio’s cross-platform support ensures consistent policy application across iOS, Android, macOS, and Windows devices.
4. Support & Maintenance Overload
Why it matters: IT teams can’t efficiently support every make/model of device users bring in.
Solution: Trio simplifies support by helping in device provisioning and real-time visibility into device health and compliance, reducing manual troubleshooting.
5. Legal & Compliance Risks
Why it matters: BYOD increases exposure to data protection laws (GDPR, HIPAA, etc.) and regulatory scrutiny.
Solution: Trio provides built-in compliance templates and audit-ready reports, helping you meet requirements with minimal overhead.
6. Loss of IT Control
Why it matters: Personal devices operate outside corporate boundaries, making it harder to enforce policies or revoke access when needed.
Solution: Trio lets you apply and enforce policies remotely, revoke app access, and retire devices securely when employees leave.
7. Employee Privacy Concerns
Why it matters: Monitoring personal devices can feel intrusive and damage trust.
Solution: Trio offers non-invasive tracking, monitoring only corporate apps or profiles while respecting personal usage.
8. Data Ownership Confusion
Why it matters: When employees save documents to personal cloud drives or email them to themselves, it blurs the line between company-owned and personal data. This creates risk during offboarding, legal discovery, or internal audits.
Solution: Trio enforces containerized data environments and blocks syncing to unmanaged cloud apps, ensuring all corporate data stays within company-controlled apps and storage.
9. Inconsistent Updates & Patch Gaps
Why it matters: BYOD devices may run outdated operating systems or unpatched apps, opening security holes or causing compatibility issues with company software.
Solution: Trio pushes over-the-air updates and version enforcement rules to ensure all connected devices run current, secure configurations, without relying on the user to update manually.
Trio gives SMB IT teams the tools to embrace BYOD without giving up control or increasing risk.
How Trio Can Help With BYOD in Your Organization
For small and medium-sized businesses, managing personal devices across a distributed workforce can feel chaotic. But with the right MDM solution, BYOD doesn’t have to mean loss of control.
Trio is built to help IT admins secure, support, and scale BYOD adoption, without complex setup or enterprise bloat. Here’s how:
| Trio Capability | What It Solves | Example Use Case |
|---|---|---|
| Security Policy Enforcement | Reduces the risk of data breaches by enforcing encryption, screen locks, and remote wipe | Auto-lock a lost phone with client data |
| Customizable Policy Engine | Ensures consistent password, app, and access settings across devices | Prevent use of unauthorized apps on BYOD |
| Application Management | Supports remote app install, removal, and over-the-air updates | Push updated productivity tools to employee phones |
| Device Visibility & Tracking | Simplifies IT asset management for both corporate and personal endpoints | Maintain inventory and usage reports for BYOD |
| Remote Support | Enables real-time MDM remote control for faster issue resolution | Troubleshoot VPN config on a remote Android device |
| Data Safeguards | Enables backup, encryption, and secure file sync | Protect sensitive sales data stored on personal tablets |
| Compliance Monitoring | Built-in tools for audits, reports, and IT compliance documentation | Generate GDPR audit logs for employee laptops |
Bonus: Trio works with your identity provider (Azure AD, Okta, etc.) to sync user roles and apply BYOD rules automatically; no duplicate config or manual mapping.
Try Trio Today
Get started with a free trial and see how easy it is to manage personal devices alongside company hardware—without compromising security or usability.
👉 Book a Demo | Start Free Trial
Conclusion
BYOD is the reality for modern businesses. While it brings clear benefits like cost savings, productivity gains, and employee flexibility, it also introduces serious operational and security challenges.
From device loss and compliance risks to data ownership confusion and patching gaps, BYOD can overwhelm lean IT teams without the right tools in place. That’s why SMBs turn to solutions like Trio to take back control.
Trio’s built-in security policies, cross-platform visibility, and automated compliance enforcement make it easier to embrace BYOD without compromise, protecting your data, users, and operations from day one.
Frequently Asked Questions About BYOD Risks & Security Challenges
1. What are the biggest BYOD risks for small businesses?
The top BYOD risks include data breaches, unauthorized access, and non-compliance with regulations like GDPR or HIPAA. Personal devices often lack enterprise-grade security, increasing the chances of sensitive information being leaked or stolen.
2. What are common BYOD threats and vulnerabilities?
BYOD threats and vulnerabilities range from malware on unmanaged devices to unsecured app usage and outdated operating systems. Without centralized control, it's difficult to detect and respond to incidents quickly.
3. What should IT admins be most concerned about with BYOD?
The primary BYOD concerns include enforcing security policies, maintaining device visibility, and balancing user privacy. Other challenges involve legal compliance, data ownership confusion, and inconsistent patching across diverse personal devices.
4. How can companies address BYOD security issues?
To tackle BYOD security issues, businesses should implement a mobile device management (MDM) platform like Trio. It enforces encryption, blocks risky apps, and applies access controls, even on personal devices, without invading employee privacy.
5. Are personal devices more vulnerable in a BYOD setup?
Yes. BYOD vulnerabilities are often tied to the lack of standardization and security hardening. Unlike company-issued devices, personal devices may run outdated software or connect to unsecured networks, exposing the organization to greater risk.
6. What are the main BYOD security challenges for IT teams?
The key BYOD security challenges include managing a wide variety of devices and OS versions, ensuring compliance across all endpoints, and protecting data without overburdening IT staff. MDM tools help automate policy enforcement and threat response.
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!





