In the rapidly evolving landscape of corporate technology, the proliferation of mobile devices poses both opportunities and challenges for organizations. Mobile Device Management implementation has become imperative, serving as a linchpin in addressing the intricate issues associated with mobile device usage within corporate environments.
This blog post aims to guide organizations in successfully navigating the complexities of MDM implementation. From bolstering security measures to optimizing operational efficiency and cost management, MDM plays a multifaceted role in ensuring control, compliance, and productivity. Join us on a journey to understand why MDM is indispensable, how it functions within organizations, and the key steps for seamless mobile device management implementation.
Why Implement MDM in Your Organization?
Organizations require Mobile Device Management (MDM) solutions to address the complex challenges associated with the widespread use of mobile devices in the corporate environment. MDM plays a pivotal role in enhancing security by implementing robust measures such as encryption, passcode requirements, and remote wipe capabilities. This ensures that sensitive data remains protected, even in the event of device loss or theft.
With the ability to enforce consistent security policies, MDM provides organizations with a centralized mechanism to mitigate risks and maintain control over their mobile device ecosystem. This is especially crucial in industries subject to strict regulatory requirements, where compliance with data protection standards is paramount. Furthermore, MDM facilitates efficient policy enforcement, offering organizations the means to configure and manage devices seamlessly, reducing the risk of security vulnerabilities, and ensuring a standardized approach to device configurations.
In addition to security considerations, MDM is indispensable for optimizing organizational efficiency. By automating device provisioning and enabling remote troubleshooting, MDM streamlines the deployment and management of mobile devices. This not only reduces the workload on IT teams but also minimizes downtime, enhancing overall productivity.
Cost management is another key benefit, as MDM allows organizations to track and manage mobile device assets effectively, optimizing resource usage and identifying opportunities for upgrades or replacements. The solution’s role in compliance, productivity enhancement, and cost-effective management positions MDM as a critical component for organizations seeking to harness the benefits of mobile technology while maintaining control, security, and operational efficiency.

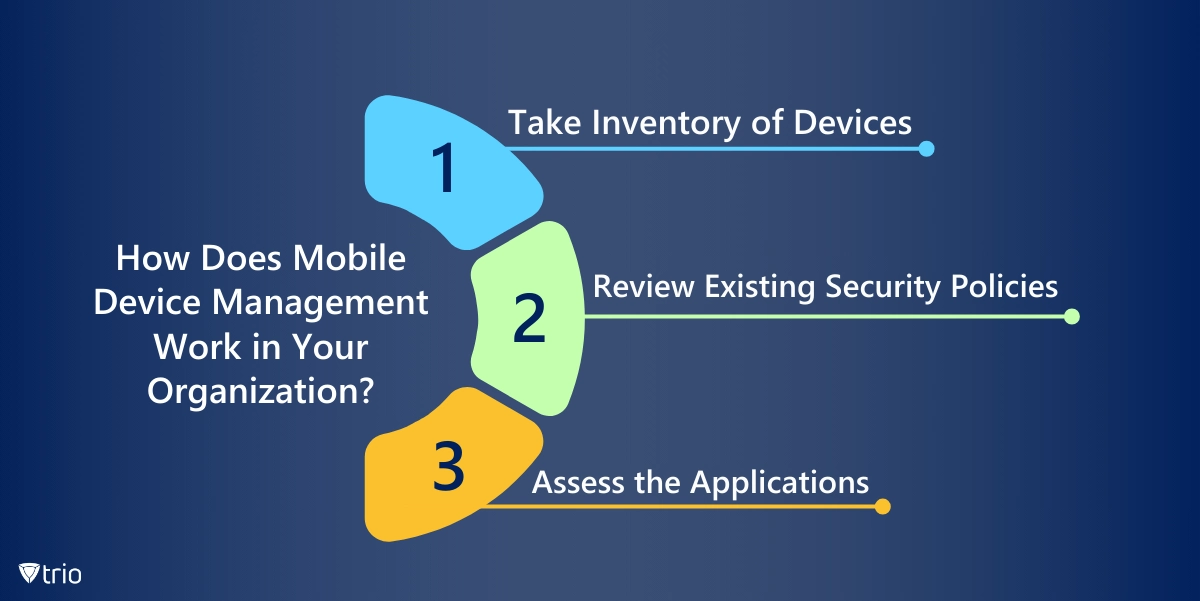
How Does Mobile Device Management Work in Your Organization?
Before learning how to implement MDM in your organization, you should first assess some things throughout your organization, across different departments and employees. This is to see what you need from an MDM solution since most MDMs are highly customizable to your organization.
Take Inventory of Devices
The first step you should take is to take inventory of the devices you already have in your organization. This includes smartphones, tablets, and any other mobile devices that may access corporate resources. This is also where you must see if your employees’ devices have access to corporate resources, which means your organization needs BYOD (Bring Your Own Device) policies.
Review Existing Security Policies
Secondly, review existing security policies and configurations applied to mobile devices. Evaluate the level of security measures in place, including password requirements, encryption settings, and access controls.
Assess the Applications
Make a list of the applications that each of your departments uses. Are they subscription-based, paid, or free? Do they need to be installed or are they used through web browsers? This list will help you to easily decide on what applications each department needs while setting up the MDM solution.
Steps to Mobile Device Management Implementation in Your Organization
Many of the steps mentioned below might not happen in this exact order or they might be merged into one step; it all depends on the MDM solution you use. Most MDM solutions have a detailed and rigorous setup that allows you to create policies, profiles, and restrictions, onboard employees, and enroll devices step-by-step. The key MDM implementation steps typically include:
1- Device Enrollment
This involves registering mobile devices with the MDM system. It can be done manually by users or automatically through device provisioning profiles.
2- Device Configuration
MDM solutions allow administrators to remotely configure device settings such as Wi-Fi, email, VPN, and security policies. This ensures that devices are set up according to organizational requirements.
3- Policy Management
MDM solutions enable the creation and enforcement of security policies on mobile devices. This includes password requirements, encryption settings, and restrictions on certain device features.
4- Application Management
MDM solutions allow administrators to distribute, manage, and update applications on mobile devices. This includes the ability to push apps, control app access, and remotely wipe app data if necessary, such as when you’re offboarding an employee.
5- Security Management
MDM solutions provide security features such as remote lock, remote wipe, and tracking of lost or stolen devices. This helps protect sensitive data and ensures compliance with security policies.
6- Content Management
MDM solutions facilitate the secure access and distribution of content on mobile devices. It may include document sharing, file synchronization, and collaboration tools.
7- Monitoring and Reporting
MDM solutions offer monitoring capabilities to track device usage, compliance with policies, and potential security threats. Reporting tools provide insights into device status and activities.
8- Identity Management
Integrating with identity management systems allows MDM solutions to enforce access controls based on user roles and permissions.
9- Over-the-Air (OTA) Updates
MDM solutions enable administrators to remotely update device firmware and software, ensuring that devices are running the latest and most secure versions.
10- Integration with Enterprise Systems
MDM solutions often integrate with other enterprise systems such as directory services, email servers, and enterprise mobility suites for seamless management.
11- Containerization
Some MDM solutions use containerization to create secure containers on devices, separating work and personal data. This helps in maintaining data privacy and security. Separating work and personal data, especially if your company has a BYOD policy is extremely important, especially for end users. The best thing to do is to be upfront and honest about the data that will be recorded or gathered with employees. Usually, when organizations are honest and reasonable with the data, they collect end users and won’t have a problem. But we strongly advise against not being transparent, especially if employees bring their own devices to work.
12- Compliance and Auditing
MDM solutions include features to check and enforce compliance with organizational policies. Auditing capabilities provide a record of device activities and changes.
Conclusion
A good MDM solution will go through all the steps mentioned above automatically while allowing you to customize each part based on your organization. One such MDM solution is Trio. While using Trio, you will be taken through a delicate, yet easy-to-understand setup of the MDM solution throughout your organization. You will be able to enroll large numbers of devices or only a small number since Trio is scalable to your organization. Afterward, you can set default policies and restrictions organization-wide, specific to a department, or even change policies and profiles based on employees. But Trio goes much further than this, allowing you to streamline the employee onboarding process. To see how Trio works and why we think it’s the best MDM solution for you, try out our free demo today!