According to a Hiscox study, “43% of cyberattacks target small businesses, costing an average of $200,000 per incident—devastating for SMBs with limited resources.” In today’s fast-moving cyberthreat landscape, small and medium-sized businesses (SMBs) face relentless attacks on their endpoints—laptops, desktops, servers, and mobile devices. For IT admins juggling limited budgets and lean teams, securing these devices is a high-stakes challenge. Endpoint Detection and Response (EDR), paired with Mobile Device Management (MDM), is your frontline defense. EDR detects and neutralizes threats in real-time, while MDM ensures mobile devices stay compliant and secure. Together, they’re a powerhouse for SMBs. Solutions like Trio’s MDM with built-in EDR deliver scalable, affordable protection, letting you focus on growth, not firefighting breaches. Here’s how to integrate EDR and MDM into your IT department to stay ahead of cyber risks.
What is EDR, and Why Should It be Paired with MDM?
EDR is a cybersecurity tool that monitors endpoints to detect and respond to threats like malware, ransomware, or unauthorized access. It tracks system processes, file changes, and network activity, using AI-driven techniques like behavioral analysis to spot danger. When a threat emerges, EDR acts fast—isolating devices, blocking processes, or alerting your team.
MDM complements EDR by managing mobile devices (smartphones, tablets) with policies for encryption, app control, and remote wipes. For SMBs, where employees often use personal devices, MDM ensures compliance without draining resources. Tools like Trio combine EDR and MDM, offering a unified platform to secure all endpoints, from laptops to iPhones, with minimal setup.
According to Verizon, cyberattacks cost SMBs millions annually, with 60% of breached businesses closing within six months. EDR and MDM together provide visibility, rapid response, and compliance, saving you from costly downtime or data leaks.
EDR vs. MDM
EDR solutions act as your 24/7 security sentry:
- Real-time behavioral monitoring of processes, files, and network traffic
- AI-driven threat hunting identifying zero-day attacks and ransomware
- Automated containment like device quarantine or process termination
Critical Gap: EDR can’t enforce device-level security policies or manage mobile endpoints effectively.
MDM serves as your central command hub:
- Enforces security postures: Encryption, OS updates, password policies
- Automates deployment: Silent installation of EDR agents
- Controls mobile risks: Remote wipe, app allowlisting, geofencing
Critical Gap: MDM lacks EDR’s deep behavioral analysis and threat-hunting capabilities.
Organizations may use both EDR and MDM solutions to comprehensively manage and secure their diverse endpoint landscape, covering both traditional computing devices and mobile devices. Unlike standalone EDR tools (e.g., CrowdStrike) or MDM-only platforms, Trio’s integrated approach saves SMBs from complex integrations and high costs. Curious About Trio’s Edge? Test Trio’s free demo to see how it simplifies endpoint security.
Why EDR and MDM Are Non-Negotiable for SMBs
Though EDR solutions differ, and what you should look for in an EDR solution depends on your organization, EDR in general plays a crucial role in enhancing an organization's cybersecurity posture. For IT admins at SMBs, securing endpoints isn’t just a task—it’s a survival strategy. Here’s why integrating EDR with MDM is critical:
1- Advanced Threat Detection
EDR solutions use advanced detection techniques to identify sophisticated and evolving threats that traditional antivirus software may miss. This includes detecting zero-day exploits, fileless malware, and other advanced attack techniques. MDM extends this to mobile devices, enforcing security policies to block risky apps or unsecured Wi-Fi. The limited budgets of SMBs mean you can’t afford multiple tools. A unified EDR-MDM solution like Trio stretches your dollar further.
2- Total Endpoint Visibility
EDR provides organizations with comprehensive visibility into endpoint activities, including process execution, file modifications, network connections, and user behaviors. This visibility helps security teams understand the security posture of their endpoints and detect anomalous or suspicious activities indicative of a potential breach. MDM adds mobile device oversight, tracking configurations, and app usage. In SMBs with lean teams, you need tools that simplify monitoring. Trio’s dashboard centralizes endpoint data, saving you hours of manual checks.
3- Real-time Response
EDR enables organizations to respond rapidly to security incidents, such as company data breaches, by initiating automated responses or providing security teams with real-time alerts and insights. This allows organizations to contain threats quickly, minimizing the potential impact of security breaches. Since a single breach can cripple an SMB’s operations, a fast response keeps the business running and customers trusting you.
4- Simplify Forensic Investigation
EDR logs detailed endpoint data, helping you trace a breach’s origin—critical for preventing repeat attacks. MDM provides similar insights for mobile devices, like identifying a rogue app. Trio’s integrated reporting makes post-incident analysis accessible, even for non-experts. SMBs rarely have dedicated forensic teams. Trio’s user-friendly tools empower your IT admin to handle investigations.
5- Compliance Requirements
Regulations like GDPR or HIPAA demand endpoint monitoring and incident response. EDR and MDM together ensure you’re audit-ready, with automated logs and policy enforcement. Trio’s compliance features streamline reporting, so you avoid fines. Compliance can overwhelm small teams in SMBs. Trio’s all-in-one platform reduces the burden, letting you focus on core operations.
| Benefit | What It Solves | SMB Example |
|---|---|---|
| Advanced Threat Detection | Stops sophisticated attacks like ransomware | Blocks fileless malware on a cashier’s POS system |
| Total Endpoint Visibility | Tracks all device activity to spot anomalies | Detects an employee downloading a risky app |
| Real-Time Response | Halts breaches before they spread | Isolates a hacked laptop in seconds |
| Simplified Forensics | Traces company data breach origins without experts | Identifies a phishing email as the attack source |
| Easy Compliance | Meets GDPR, HIPAA with minimal effort | Generates audit-ready logs for regulators |

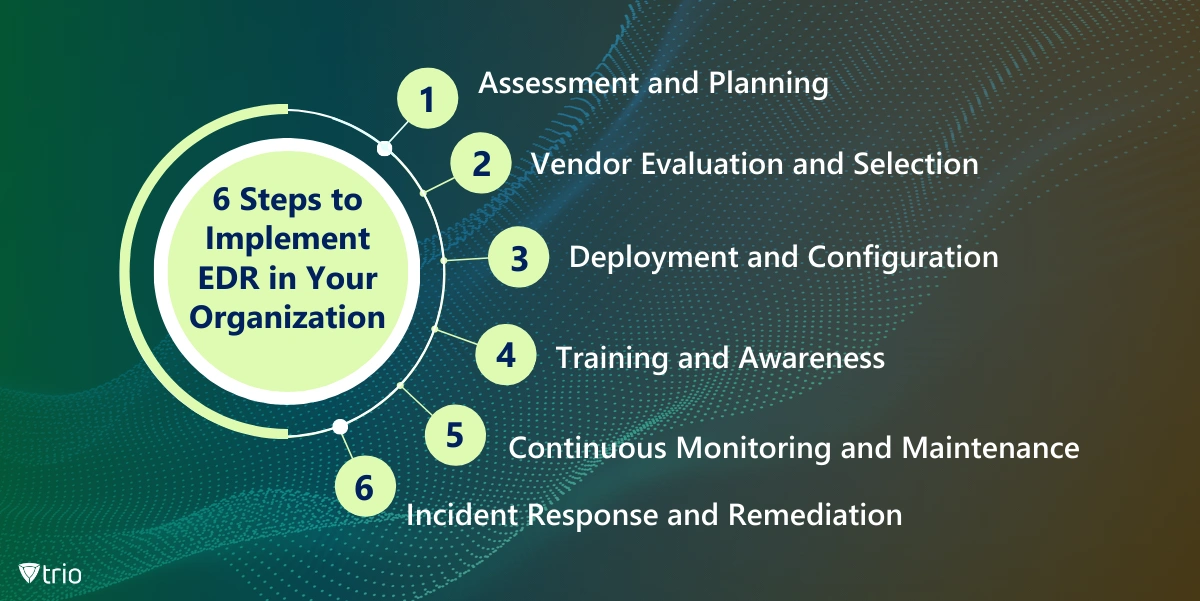
6 Steps to Implement EDR in Your Organization
Implementing EDR cybersecurity in an organization involves several key steps:
1. Assessment and Planning
Assess your organization's current endpoint security posture, including existing security tools, policies, and procedures. Identify the specific security challenges and risks your organization faces, such as common attack vectors, sensitive data assets, and compliance requirements. Develop a comprehensive plan for implementing EDR, including goals, timelines, budget considerations, and resource requirements.
- Inventory all endpoints: Use free tools like Lansweeper to identify:
- Corporate laptops
- BYOD smartphones
- IoT devices (printers, POS systems)
- Prioritize threat scenarios:
- "Remote accountants accessing QuickBooks on public Wi-Fi"
- "Shared warehouse tablets with admin privileges"
- Define non-negotiables:
- "98% agent coverage in 72 hours"
- "Zero unencrypted mobile devices"
2. Vendor Evaluation and Selection
Research EDR vendors and solutions to identify those that best meet your organization's requirements and budget. Evaluate key features such as threat detection capabilities, real-time response capabilities, scalability, ease of deployment and management, integration with existing security tools, and vendor support. Consider conducting proof-of-concept (POC) evaluations or pilot deployments to assess the effectiveness of selected EDR solutions in your environment. Trio offers all this, plus budget-friendly pricing for SMBs.
- Demand these integrations:
- Unified console (single dashboard)
- Bi-directional APIs (automate workflows)
- Lightweight agents (<3% CPU impact)
- POC Test Checklist:
- Push EDR agent to 20+ device types via MDM
- Simulate ransomware: Verify auto-quarantine + mobile lock
- Generate compliance report in <2 clicks
3. Deployment and Configuration
Deploy the chosen EDR solution across your organization's endpoints, including desktops, laptops, servers, and mobile devices. Configure the EDR solution according to best practices and your organization's specific security requirements. Integrate the EDR solution with existing security tools and systems, such as Security Information and Event Management (SIEM) platforms, threat intelligence feeds, and incident response processes. Trio’s plug-and-play setup takes hours, not weeks, making it perfect for time-strapped SMBs.
Leverage MDM as your deployment engine
- Onboard devices via email/QR code enrollment
- Silently deploy EDR agents (zero user interaction)
- Enforce baseline policies:
- Full-disk encryption
- Biometric screen locks
- Block untrusted app stores
4. Training and Awareness
Provide training and awareness programs for IT staff, security personnel, and end-users on how to use and benefit from the EDR solution. Educate stakeholders about the importance of endpoint security, common threats, and best practices for preventing and responding to security incidents.
5. Incident Response and Remediation
Establish incident response procedures and workflows for quickly responding to and mitigating security incidents detected by the EDR solution. Regularly conduct incident response drills and exercises to test the effectiveness of your response capabilities and identify areas for improvement. Document lessons learned from security incidents and use them to refine your incident response processes and enhance your overall security posture.
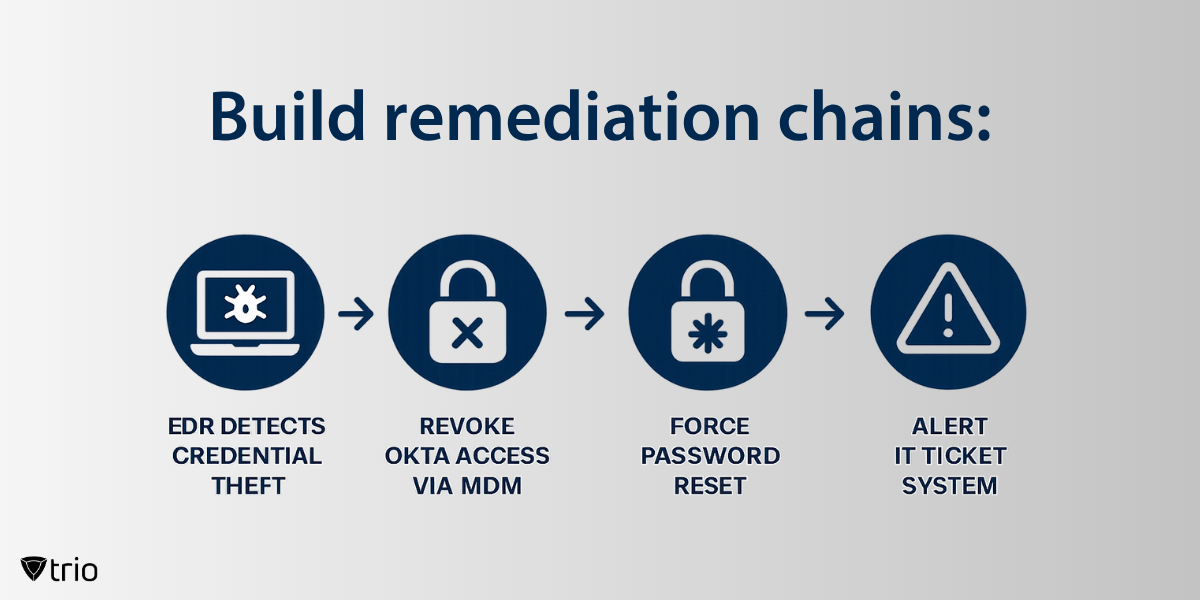
6. Continuous Monitoring and Maintenance
Continuously monitor the performance and effectiveness of the EDR solution in detecting and responding to security threats. Regularly update and patch the EDR solution to ensure it remains effective against evolving threats and vulnerabilities. Conduct periodic security assessments and audits to identify areas for improvement and optimization.
The Cost of Not Integrating EDR and MDM Solutions in Your IT Department
Ignoring endpoint security isn’t an option for SMBs. A single breach can cost significantly, draining your team’s time and eroding customer trust. Without EDR and MDM, you’re exposed to:
- Data Theft: Hackers accessing customer records or trade secrets.
- Ransomware: Locked systems halt operations for days.
- Fines: Non-compliance with GDPR or HIPAA can cost thousands.
- Reputation Loss: Customers leaving after a publicized breach. Trio’s integrated platform mitigates these risks affordably, letting you avoid catastrophe.
Among Trio’s many features, it monitors endpoints for security threats, unusual network behavior, unauthorized access, and malicious files. Its EDR technology offers real-time visibility and quick response to security incidents. It isolates affected endpoints, terminates malicious processes, and removes associated threats.
When Trio’s EDR feature is combined with its many other capabilities it becomes clear that Trio is one of the best applications to facilitate IT risk management, including vulnerability management on the market today. To experience what we’re talking about, feel free to try out Trio’s free demo.
Conclusion: The New SMB Security Mandate
For resource-strapped businesses, EDR+MDM integration isn’t about luxury; it’s about survival. The convergence of sophisticated attacks, mobile workforces, and crushing compliance demands makes this duo non-negotiable.
Results you’ll achieve:
- ⏱️ 87% faster breach containment
- 📉 60% reduction in security management costs
- ✅ 100% audit-ready compliance status
"In cybersecurity, half-measures equal full failures. Unified protection isn’t an option – it’s the price of admission."
Ready to see how a unified MDM+EDR platform can safeguard your SMB? Try Trio’s free demo, or check out Trio’s free trial to fully experience the solution in action today!
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!





