Cybersecurity threats are rampant in today's digital landscape. The growth of cyber threats necessitates the implementation of a robust Cybersecurity Incident Response Plan (CIRP). This comprehensive guide aims to provide IT administrators with an in-depth understanding of establishing an effective Cyber Incident Response Plan.
What Is a Cybersecurity Incident Response Plan?
A Cybersecurity Incident Response Plan is a well-structured approach that outlines the handling and management of cybersecurity incidents. The goal is to identify, manage, and reduce the damage of cybersecurity threats effectively. Besides, it helps in preventing similar future incidents, thereby supporting business continuity.
Importance of Cybersecurity Incident Response Plan
An effective CIRP is crucial in today's digital era for several reasons.
Protection of Sensitive Data
Organizations handle sensitive data regularly. A robust CIRP ensures the confidentiality of crucial business and customer information, protecting it against potential data breaches.
Business Continuity
A CIRP enables IT systems to remain operational, preventing data loss. This is crucial for business continuity, as disruptions in IT operations can lead to downtime, financial losses, and reputational damage.
Prevention of Financial Loss
Cybersecurity threats and IT failures can result in significant financial losses. A CIRP aims to minimize the impact of such incidents, protecting an organization's financial assets, and ensuring the cost-effectiveness of IT operations.
Maintaining Reputation and Trust
A security breach or data loss can damage an organization's reputation and erode customer trust. An effective CIRP helps prevent such incidents, contributing to the maintenance of a positive image and trust among stakeholders.

IT and Tech Industry Cybersecurity Incident Response Plan Templates
The IT and Tech industry requires a robust and systematic approach when responding to cybersecurity incidents. Here are some of the top incident response plan templates and resources that can be utilized to enhance your organization's cybersecurity posture:
Key Components of an Incident Response Plan Template
- Purpose and scope: Outlines why the plan exists and its coverage.
- Threat scenarios: Identifies potential incidents that could affect the organization.
- Roles and responsibilities: Defines duties of stakeholders involved in the incident response process.
- Incident response process: A step-by-step guide from detection to post-incident review.
Notable Incident Response Plan Templates
These incident response policy examples provide a structured approach to developing an effective incident response plan tailored to the unique needs of the IT and Tech industry. You can incorporate these resources in your organization’s cybersecurity incident response training, planning, executing, and reviewing cybersecurity incidents more effectively, ultimately enhancing your resilience against cyber threats.
Cynet Incident Response Plan Template
Focuses on team responsibilities, testing, process overview, and includes incident response checklists.
NIST Incident Response Plan Template
Offers a comprehensive framework with steps like preparation, detection/analysis, containment/eradication/recovery, and post-incident activity.
Berkeley University Incident Response Template
Includes IT systems overview, security definitions, contact people, and incident response procedures.
IltaNet Incident Response Plan
Covers team responsibilities, notifications, types of incidents, and recovery strategies.
Downloadable in .ASHX format.
Thycotic Incident Response Template
Details roles, responsibilities, threat classification, and phases of incident response.
Requires registration to obtain the .DOC file.
Sysnet Security Incident Response Plan Template
Emphasizes recognition of security incidents, roles and responsibilities, and incident response steps.
Downloadable after registration in .DOC format.
California Government Department of Technology Incident Response Plan
Features a 17-step incident response procedure, with details for specific incident types like malware and system failure.
I-Sight Incident Response Template
Includes purpose, scope, definitions of incidents, roles & responsibilities, and incident response stages.
Requires registration to access the .DOC file.
Execution Strategies in IT Cybersecurity Incident Response Plan
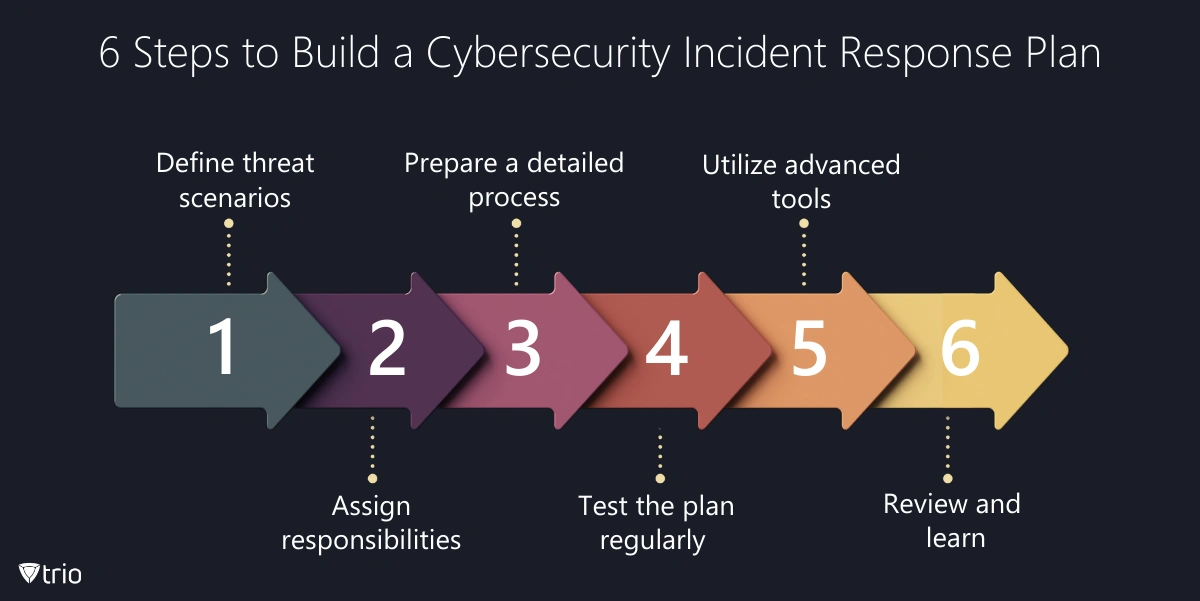
- Create a simple, well-defined process: Ensure the response plan is easy to follow.
- Create a communication strategy: Clearly define communication protocols for informing stakeholders.
- Use an incident response plan template: Adapt industry templates to your organization's needs.
- Put your incident response plan to the test: Conduct drills to ensure effectiveness.
- Use a centralized approach: Centralize information for efficient incident response.
Team Roles and Responsibilities in Cybersecurity Incident Response
- Incident Response Manager: Oversees actions during the incident.
- Security Analysts: Research the details of an incident.
- Threat Researchers: Provide threat intelligence and context.
- Human Resources, Audit and Risk Management Specialists, General Council, Public Relations: Play specific roles in the incident response process.
Post-Incident Review Best Practices in IT Cybersecurity Incident Response
- Decide which incidents need review: Use severity levels to trigger reviews.
- Draft your review promptly: Ideally, within 24-48 hours post-incident.
- Assign roles and owners: Designate specific individuals to draft the review.
- Work from a template: Ensures consistency and completeness.
- Include a timeline: Detail the sequence of events.
- Add details and capture incident metrics: Provide a comprehensive account and measure impact.
- Establish a blameless culture: Encourage open sharing of information.

The Six Steps of IT Risk Management
A systematic approach to IT Risk Management involves six crucial steps.
Step 1: Examine Data Categories
Understanding the different types of data that your organization handles is crucial. This step involves categorizing and classifying data based on its sensitivity and importance.
Step 2: Assess and Prioritize Information Risks
After identifying vulnerabilities and analyzing data types, your organization needs to evaluate and prioritize the risks associated with potential threats.
Step 3: Define Risk Tolerance
Your organization needs to define its risk tolerance, which is the acceptable level of risk you are willing to take. Once this is established, they can create and implement CIRP processes and policies that align with your risk tolerance.
Step 4: Address Current Risks
With a clear understanding of current vulnerabilities and risks, your organization can develop and implement strategies to mitigate or reduce these risks.
Step 5: Utilize Data Security Solutions
Implementing robust data security solutions is crucial for protecting sensitive information. This could include encryption, access controls, intrusion detection systems, and other technologies that help safeguard data from unauthorized access or manipulation.
Step 6: Maintain Ongoing Risk Surveillance
IT risk management is an ongoing process. Continuous monitoring involves staying vigilant, regularly assessing the effectiveness of risk mitigation measures, and adapting strategies to address new and emerging threats.
The Trio MDM Solution
The Trio MDM solution is an innovative tool that can benefit IT administrators and business owners. The MDM solution provides control and oversight over the use of smartphones, tablets, and other mobile devices, ensuring that they adhere to security policies and protocols.
The solution is highly useful for incident response teams. By implementing the Trio MDM solution, organizations can quickly identify, assess, prioritize, and mitigate risks associated with the use of information technology within an organization.
Try out Trio’s free demo and see how you can make a difference in mitigating and managing IT risks.
Cyber Incident Response Plan: Conclusion
The importance of a Cybersecurity Incident Response Plan in today's digital era cannot be overstated. With cyber threats escalating, it is critical for organizations to have a solid plan in place. By understanding the importance, steps involved, and leveraging advanced solutions like Trio MDM, your organization can fortify its digital foundations for sustained success.
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!





