In an era where data breaches make headlines daily and cyber threats evolve rapidly, organizations can’t afford to overlook the security of sensitive customer data. As an IT admin at an SMB, achieving SOC 2 compliance is critical to secure your business’s data, earn customer trust, and meet regulatory demands with limited resources. Developed by the American Institute of CPAs (AICPA), SOC 2 sets rigorous standards for managing and securing cloud-based data, ensuring your organization is equipped to handle the complexities of today’s digital environment. This guide dives deep into what SOC 2 compliance entails, why it’s essential, and how solutions like Trio can simplify the journey.
What Is SOC 2 Compliance?
SOC 2 (Service Organization Control 2) is a framework designed by the AICPA to ensure service providers, such as SaaS companies, data centers, and managed service providers, securely manage customer data stored in the cloud. Unlike other compliance standards, SOC 2 focuses on five Trust Service Criteria: security, availability, processing integrity, confidentiality, and privacy. These principles guide organizations in implementing controls to safeguard data and ensure system reliability. Here’s a detailed breakdown:
- Security: Ensures systems are protected against unauthorized access, both physical and digital. For instance, a cloud provider might implement multi-factor authentication and encryption to meet this criterion.
- Availability: Guarantees systems are operational and accessible as agreed upon. This is critical for businesses relying on uptime, like e-commerce platforms.
- Processing Integrity: Ensures data processing is complete, accurate, and timely. A payroll processor, for example, must ensure error-free calculations to comply.
- Confidentiality: Protects sensitive information from unauthorized disclosure. This is vital for law firms handling client contracts.
- Privacy: Addresses the collection, use, and disposal of personal data, aligning with regulations like GDPR. A healthcare app, for instance, must secure patient data to meet this criterion.
To achieve SOC 2 compliance, organizations undergo an independent audit by a third-party auditor. A successful audit results in an SOC 2 certification, a powerful signal to customers and partners of your commitment to data security. For example, as an IT admin at an SMB, SOC 2 certification assures your clients that their sensitive data, like customer records, is protected against breaches.

Why Is SOC 2 Compliance Important?
SOC 2 compliance offers numerous benefits that make it indispensable for organizations handling sensitive data:
- Enhanced Data Security: SOC 2 mandates robust controls to prevent unauthorized access, reducing the risk of costly data breaches. For instance, as an IT admin at an SMB, you can protect sensitive customer data, like payment information, from cyber threats.
- Customer Trust: Certification signals to clients that their data is handled securely, fostering confidence. As an SMB IT admin, SOC 2 compliance helps you assure clients and partners that your systems are secure, winning their trust and contracts.
- Regulatory Alignment: SOC 2 helps meet industry-specific requirements and IT compliances, such as HIPAA for healthcare or PCI DSS for payment processing, avoiding legal penalties.
- Risk Mitigation: Implementing SOC 2 controls helps organizations in identity and assessment management. This in turn mitigates risks related to data security and privacy. By adhering to SOC 2 standards, companies can better protect themselves from potential security incidents and the associated financial and reputational damages.
- Competitive Edge: SOC 2 compliance differentiates your business in crowded markets. A managed service provider showcasing SOC 2 certification can attract security-conscious clients.
Curious about how SOC 2 compares to other standards? Check out our detailed comparisons: SOC 1 vs. SOC 2 and ISO 27001 vs. SOC 2.

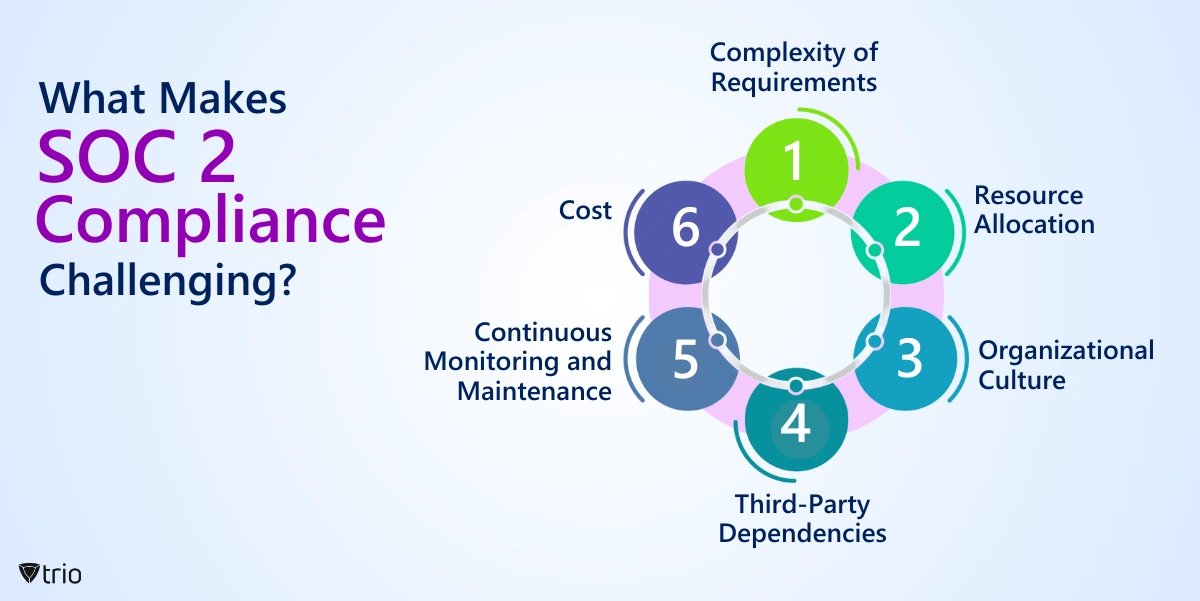
What Makes SOC 2 Compliance Challenging?
While the benefits are clear, achieving SOC 2 compliance can be daunting. Here are the key hurdles and how to address them:
- Complex Requirements: The five Trust Service Criteria require comprehensive controls, which can overwhelm organizations with limited expertise. Partnering with compliance experts can streamline this process.
- Resource Demands: Audits, risk assessments, and control implementation require significant time and budget. As an SMB IT admin, you can prioritize high-impact controls, like access management, to achieve SOC 2 compliance without straining your limited budget.
- Cultural Shifts: Embedding security into daily operations demands employee training and process changes. Regular workshops can foster a compliance-focused culture.
- Third-Party Risks: Vendors must also meet SOC 2 standards, necessitating thorough due diligence. Contracts should include compliance clauses to ensure accountability.
- Ongoing Maintenance: Compliance requires continuous monitoring to address new threats. Automated tools can simplify regular assessments.
- Cost: As an SMB IT admin, audit and technology costs can challenge your budget, but phased implementation helps manage expenses effectively. Phased implementation can spread costs over time.
How Is SOC 2 Compliance Relevant to MDM Solutions?
SOC 2 compliance is relevant to Mobile Device Management (MDM) solutions in several ways:
1. Data Security
MDM solutions are responsible for managing and securing mobile devices, including smartphones, tablets, and laptops, that access sensitive corporate data. As an SMB IT admin, using an MDM solution like Trio to secure employee devices ensures SOC 2 compliance, protecting client data and meeting regulatory requirements.
2. Availability
MDM solutions play a critical role in ensuring the availability of corporate data and applications on mobile devices. SOC 2 compliance requires MDM providers to demonstrate the availability of their services and infrastructure to meet customer needs and expectations.
3. Processing Integrity
MDM solutions must ensure the integrity of data processing activities, such as device provisioning, configuration, and monitoring. SOC 2 compliance ensures that these processes are performed accurately, reliably, and securely to prevent data manipulation or unauthorized changes.
4. Confidentiality
MDM solutions handle sensitive corporate information stored on mobile devices, such as emails, documents, and business applications. SOC 2 compliance requires these solutions to implement controls to maintain the confidentiality of this data and prevent unauthorized access or disclosure.
5. Privacy
MDM solutions often collect and process personal information about device users, such as contact details, location data, and usage patterns. SOC 2 compliance mandates that these solutions have measures in place to protect the privacy rights of individuals and comply with applicable privacy regulations, such as GDPR or CCPA.
6. Vendor Risk Management
Organizations that use MDM solutions need assurance that their vendors adhere to strict security and compliance standards. SOC 2 compliance provides a framework for evaluating and managing the risks associated with MDM providers, ensuring that they meet the necessary security and privacy requirements.
Download Our Free SOC 2 Compliance Checklist
Ensuring compliance with SOC 2 standards is crucial for maintaining trust and security in your organization. To simplify the process, we’ve put together a practical SOC 2 checklist that covers key requirements, from security controls to audit readiness. Whether you’re preparing for an audit or strengthening your internal processes, this checklist will help you stay on track. Download it below and streamline your SOC 2 compliance journey!
Conclusion
In conclusion, SOC 2 compliance stands as a cornerstone in today's digital landscape, offering a robust framework for organizations to safeguard sensitive data, build trust with customers, meet regulatory obligations, manage risks effectively, and gain a competitive edge in the market. While achieving SOC 2 compliance poses significant challenges, from the complexity of requirements to resource allocation and continuous monitoring, the benefits far outweigh the costs. Moreover, the relevance of SOC 2 compliance extends beyond traditional IT infrastructure to encompass emerging technologies like MDM solutions, where data security, availability, processing integrity, confidentiality, privacy, and vendor risk management are paramount.
An MDM solution that can guarantee your organization’s compliance with SOC 2 and other important IT compliance is Trio. Trio is capable of helping you comply with the following protocols:
- SSO (Single Sign-On)
- SCIM (System for Cross-domain Identity Management)
- GDPR (General Data Protection Regulation)
- SOC2 (Service Organization Control 2)
- CIS (Center for Internet Security)
- EDR (Endpoint Detection and Response)
- VPN (ZTNA)
- VPP (Volume Purchase Program)
- APNs Certificate (Apple Push Notification service)
- ADE (DEP) (Automated Enrollment Program)
- NIST (National Institute of Standards and Technology)
We recommend you try out Trio’s free demo today and see how compliance with universal standards has never been easier. By embracing SOC 2 compliance and integrating its principles into their operations, organizations can navigate the complexities of the digital age with confidence, knowing that they are equipped to protect their most valuable asset – their data. Check out Trio’s free trial today!
Get Ahead of the Curve
Every organization today needs a solution to automate time-consuming tasks and strengthen security.
Without the right tools, manual processes drain resources and leave gaps in protection. Trio MDM is designed to solve this problem, automating key tasks, boosting security, and ensuring compliance with ease.
Don't let inefficiencies hold you back. Learn how Trio MDM can revolutionize your IT operations or request a free trial today!





